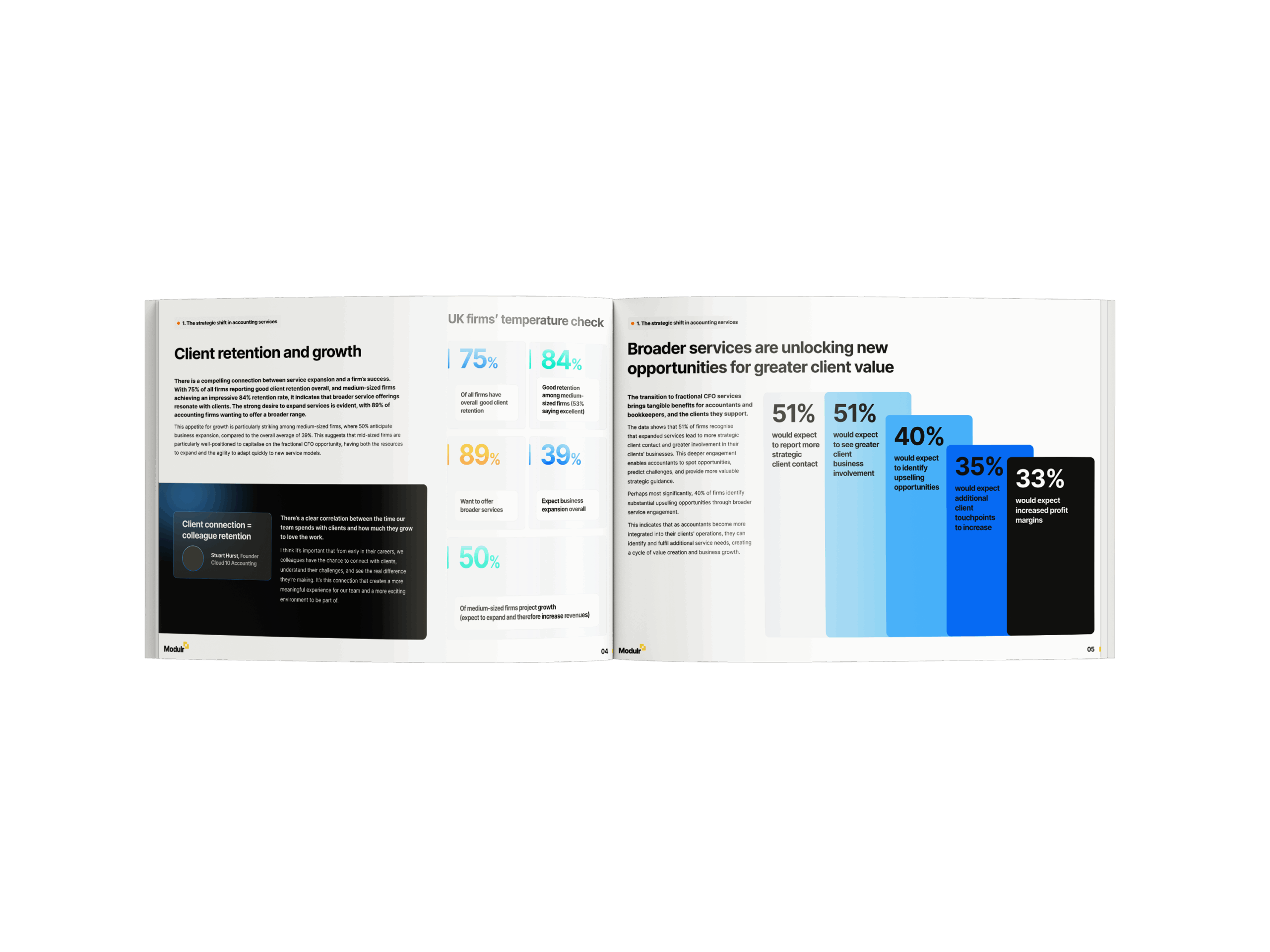
As APP fraud grows more sophisticated, banks must move beyond transactional checks and use behavioural signals to intervene before money moves.
Authorised push payment (APP) fraud is no longer a fringe threat—it’s now the most advanced form of digital deception today. And it’s growing smarter, faster, and more personal.
Last year, losses exceeded £450 million in the UK alone. Victims sent the money themselves, but they were being manipulated.
To many, that makes APP scams seem unsolvable. But they’re not. Most of these scams don’t begin with a phone call; they begin long before, with reconnaissance, setup, and signals that can be detected in the session or across prior ones.
APP fraud persuades, it doesn’t breach
In today’s scams, criminals no longer force their way in. They guide victims to act, coaching them through transferring money themselves. But behind the emotional manipulation sits something more calculated: technology used to enable and scale the con.
Spoofed websites make fake interfaces look convincing. Remote access tools give scammers control behind the scenes. Deepfakes and scripted voice calls build credibility and urgency. Each part of the scam is designed to feel real and work.
But this kind of fraud doesn’t happen in a single moment. It unfolds in stages: reconnaissance, session manipulation, and remote access. Each stage is supported by tech, and each stage leaves behind signals.
With the right telemetry in place, these signals can be detected. With session intelligence, they can be acted on before the payment is made, while the scam is still unfolding.
Why traditional defences fall short
Most fraud detection systems are designed to catch anomalies after the fact: unusual transactions, flagged devices, or known malware. But APP scams don’t always look suspicious. The victim logs in, uses their own device, and authorises the payment. But APP fraud slips through the cracks because it doesn’t look suspicious on the surface.
The customer logs in as usual. They’re on their own device. The payment is authorised. Everything appears normal until it’s not. That’s because the real signals aren’t in the transaction. They’re in the journey leading up to it, and most banks simply aren’t looking there.
What banks need is a mindset shift
APP fraud doesn’t rely on unauthorised access. The user logs in, uses their own device, and completes the transaction. Everything appears genuine until it’s too late.
But that doesn’t mean the signals weren’t there.
With the right telemetry, banks can observe:
- Remote access taking place
- Concurrent voice calls or manipulation
- Unusual typing behaviour or rushed navigation
- Anomalies in how users typically interact with their accounts
Individually, these might not set off alarms. But together, they tell a story—a story of someone being manipulated.
This is where the shift begins: from reactive fraud detection to proactive contextual insight. It’s not just about better tools, it’s about asking better questions earlier in the customer journey.

Fraud is a journey, so prevention must be too
APP fraud doesn’t begin at the point of payment. It starts much earlier and doesn’t end when the money moves.
Each scam unfolds across multiple stages, and each one presents a chance to act:
- Before the fraud: Phishing attempts, leaked credentials, session anomalies.
- During the scam: Abnormal navigation, remote access, rushed payments.
- After the scam: Links to mule accounts, cross-channel signals, repeat patterns.
With real-time visibility, banks can trace this journey and spot opportunities to intervene before it’s too late.
Trust is earned through protection, not just reimbursement
Regulators like the UK PSR are already shifting liability back to banks, even for authorised payments. But customer expectations go further: they don’t just want their money back, they want to feel safe.
To protect customers, banks must stop treating fraud as a back-office problem and start thinking like behavioural analysts. The earlier they act, the stronger their defences and the safer their customers.
Proactive protection is no longer optional. It’s a competitive advantage.