There are already several families of banking malware for Android that we have seen appear at the beginning of 2021, such as Toodler, Oscorp, and now, FluBot.
Although in the first few versions of FluBot, its developers seemed to be mainly interested in stealing the credentials of clients of Spanish entities, over the months new versions have been detected that have been distributed in campaigns in other European countries.
Even in the latest versions, samples prepared for use in campaigns in Japan have been found, which include a different seed for the DGA and strings in Japanese for the fake messages that are shown to the victim.
Without a doubt, the expansion to other countries that we’re seeing, especially in recent weeks, tells us that we’re probably facing what could become one of the most active bankers this year.
Currently, versions have been detected that are used in campaigns in Spain, the United Kingdom, Hungary, Poland, Norway, Italy, Denmark, the Netherlands, Germany, Sweden, Finland, and Japan. Based on what has been observed so far, the list of affected countries is expected to continue growing.
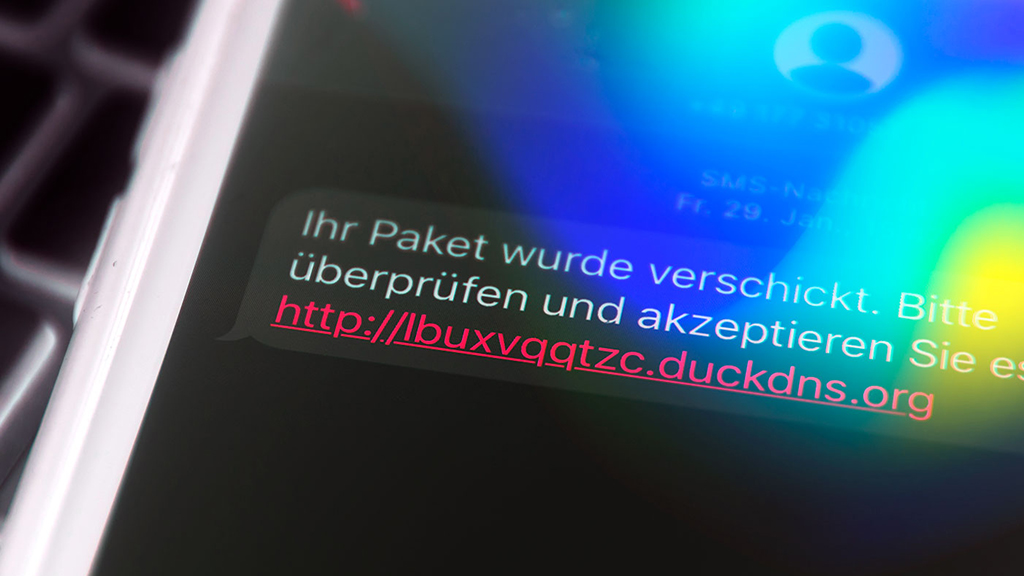
The distribution of this banking trojan is one of its main strengths since the use of text messages impersonating delivery services companies is a really good idea for deceiving the victims and getting them to install the malicious application.
In addition, for attackers, the cost is non-existent, since they are using the infected phones to send these messages to the numbers that they collect with each infection. This is especially problematic for the user, since not only could their credentials be stolen, but they will have to pay for the sending of the fraudulent messages that are sent without them even realizing it.
Beyond the propagation strategy and the DGA implementation, FluBot is just another Android banker, whose credential-stealing strategy is the same as the rest: phishing web injections (overlays) that are displayed when it detects the opening of the legitimate application through accessibility events.
Thanks to the accessibility permissions, this trojan is not only capable of detecting the opening of the affected applications to show the injections, but it is also capable of logging and sending the different events that occur in the interface to the attackers’ server, including those related to changes in the text fields, thus being able to steal credentials while the user types them in.
In addition to the main functionality of stealing credentials, FluBot also includes functionality to steal other data found on the device, which is the same as with many other families of bankers for Android. The theft of the contact list, mainly to continue spreading the trojan, and the theft of the received text messages to have access to the one-time authorization codes, are some of the functionalities implemented by this malware beyond the theft of credentials.
The presence of an algorithm that generates the domain names used by the control server every month, together with the use of asymmetric encryption to mainly verify that it’s a server controlled by the developers, are the main elements that differentiate FluBot from the other banking trojans for Android.
As mentioned previously, we have already seen three new families at the beginning of the year, which makes us think that we could see more throughout the year.
Although, without a doubt, what we will see will be new samples of FluBot throughout this year, and based on what we’ve seen so far, we will surely see new campaigns affecting users in countries beyond those currently affected today.
Therefore, we must keep a close eye on any developments that we are likely to continue to see this year.







Log in to access complimentary passes or discounts and access exclusive content as part of your membership. An auto-login link will be sent directly to your email.
We use an auto-login link to ensure optimum security for your members hub. Simply enter your professional work e-mail address into the input area and you’ll receive a link to directly access your account.
Instead of using passwords, we e-mail you a link to log in to the site. This allows us to automatically verify you and apply member benefits based on your e-mail domain name.
Please click the button below which relates to the issue you’re having.
Sometimes our e-mails end up in spam. Make sure to check your spam folder for e-mails from The Payments Association
Most modern e-mail clients now separate e-mails into different tabs. For example, Outlook has an “Other” tab, and Gmail has tabs for different types of e-mails, such as promotional.
For security reasons the link will expire after 60 minutes. Try submitting the login form again and wait a few seconds for the e-mail to arrive.
The link will only work one time – once it’s been clicked, the link won’t log you in again. Instead, you’ll need to go back to the login screen and generate a new link.
Make sure you’re clicking the link on the most recent e-mail that’s been sent to you. We recommend deleting the e-mail once you’ve clicked the link.
Some security systems will automatically click on links in e-mails to check for phishing, malware, viruses and other malicious threats. If these have been clicked, it won’t work when you try to click on the link.
For security reasons, e-mail address changes can only be complete by your Member Engagement Manager. Please contact the team directly for further help.